Reverse-engineering the ABUS Secvest Wireless Intruder Alarm System's Radio Protocol
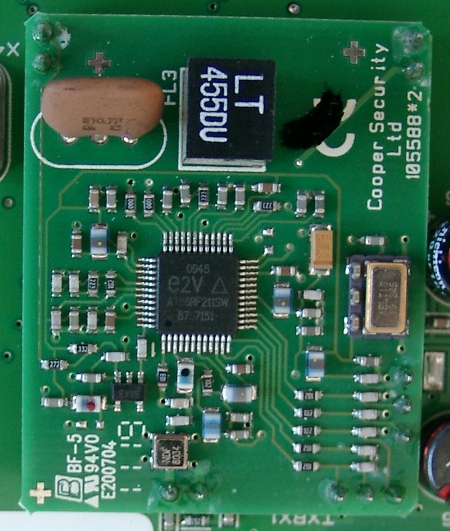
May 10, 2012 at 01:00 AM | categories: reverse engineering, wirelessThis report documents an analysis of the wireless interface of an ABUS Secvest burglar alarm system. The analysis is based on passively received radio datagrams, which were reverse-engineered. Because the protocol offers no protection mechanism against attacks, the Secvest system cannot grant confidentiality, integrity, and authenticity of communication. This is a security weakness, especially if messages are transmitted via a shared and remotely accessible medium.
Until now there is no public review available in which the effective protection level of the Secvest system is examined. The weak link is the system’s wireless interface: ABUS doesn’t use encryption and message authentication and not even a simple rolling code, which is a common technique even for garage door openers. The lack of protection mechanisms allows an attacker to eavesdrop radio communication and to inject their own datagrams by spoofing addresses of components belonging to an alarm system.
IT security testing services
Over at Pentagrid, we provide pentesting services.
Latest blog posts
- Penetration testing services
- Simple server and service availability testing script with SMS notification
- Konferenz des DKI zu IT-Sicherheit im Krankenhaus
- Forensik-Challenge des Bundesnachrichtendienstes
- Fensterbrief - a python script for working with letters based on LaTeX and Markdown
- Traveling like a pro – an eight step guide to master business trips in Europe and to avoid common pitfalls
- Update
- JointSpace Server Directory Traversal Vulnerability on a Philips 6000 Series Smart LED TV
- Stack-based Buffer Overflow in the VPN Software tinc for Authenticated Peers
- Erster Platz beim Univention Absolventenpreis 2012
Categories
- advisory (2)
- aktenvernichtung (1)
- bnd (1)
- degate (1)
- forensik (1)
- general (5)
- latex (1)
- reverse engineering (4)
- tools (4)
- wireless (1)
